Robert Triggs / Android Authority
TL;DR
- Apple is rolling out critical security updates to iOS 15 and iOS 16, patching an iMessage flaw that was used to plant spy ware on iPhones.
- The exploit was used on iPhones operating iOS 15.7 and earlier. iOS 16 had different adjustments that protected it from this cyberattack.
- iPhone and iPad customers are beneficial to replace their units instantly.
Apple prides itself on the security and privateness offered by iPhones, and to a very good extent, we do agree that it’s higher than Android. However, iPhones are comparatively safe, and not completely safe. The proof for this assertion lies with the brand new iOS 16.5.1 replace that’s rolling out to iPhones, bringing an pressing repair for a critical iMessage security flaw. If you personal an iPhone, we strongly suggest updating your telephone straight away.
Apple is rolling out iOS 16.5.1 and iPadOS 16.5.1 to customers. The major repair talked about within the changelog is a repair for a difficulty that prevented charging with the Lightning to USB 3 Camera Adapter.
However, the changelog additionally mentions “important security fixes,” that are highlighted in a separate doc. These two security flaws pertain to the “Triangulation” cyberattack that was highlighted by Eugene Kaspersky, the CEO of Kaspersky, earlier this month.
As The Washington Post mentions, the security flaw was used to hack 1000’s of units, together with these of Kaspersky’s senior staff.
The Triangulation assault labored by sending an iMessage with a malicious attachment. The person doesn’t have to see the message and even open it for the spy ware to be planted on the iPhone.
The spy ware then transmits personal data akin to microphone recordings, pictures from IM apps, geolocation, and different information to distant servers. It may even extract passwords from Apple’s keychains, and modify and export recordsdata.
Edgar Cervantes / Android Authority
The security flaw is separate from previous iOS exploits akin to Pegasus, Predator, or Reign. Among different methods, it’s totally different from these as there are a couple of methods to already defend your self.
One, disabling iMessage would forestall your telephone from being contaminated. Two, for the reason that spy ware on this occasion resides within the reminiscence of the iPhone, merely turning an contaminated iPhone off and on once more would “cure” it from the spy ware (till it will get re-infected). Third, Apple additionally has an elective Lockdown Mode out there in iOS that might block the assault.
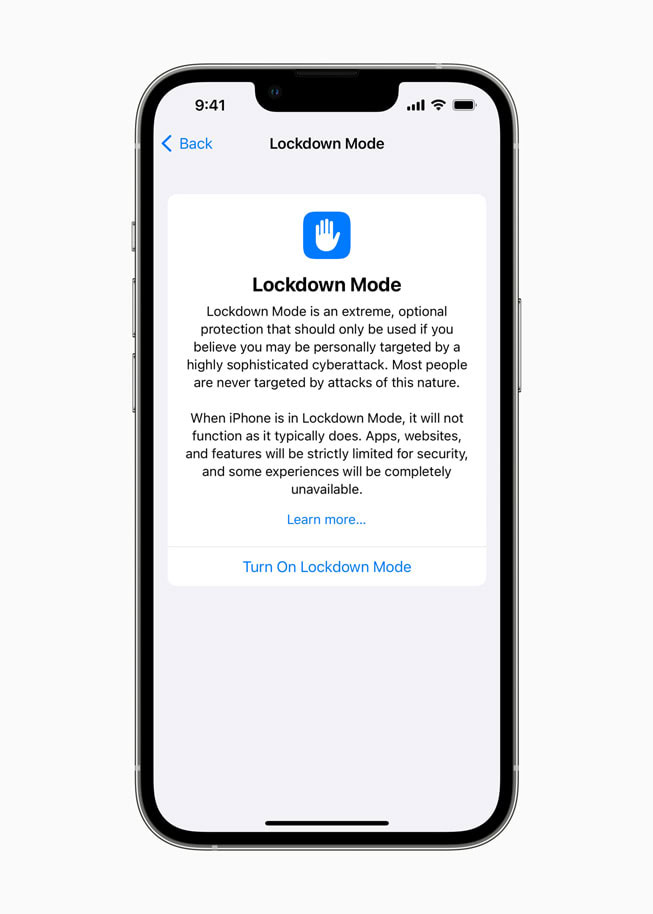
In The Washington Post‘s report, Apple claims that the attacks were only possible on iOS 15.7 and earlier, as newer versions of the OS had other improvements that would make them impervious to the attack. Further, 90% of customers who bought devices in the past four years had already updated to iOS 16.
For users who do not want to (or cannot) update to iOS 16, Apple is also rolling out iOS 15.7.7 and iPadOS 15.7.7 which include the same security fixes present on iOS 16.5.1 and iPadOS 16.5.1 respectively.
We’ve reached out to Apple for a remark. We’ll replace the article after we hear again from them.

