Getty Images
If your group makes use of servers which are outfitted with baseboard administration controllers from Supermicro, it’s time, as soon as once more, to patch seven high-severity vulnerabilities that attackers could exploit to realize management of them. And sorry, however the fixes should be put in manually.
Typically abbreviated as BMCs, baseboard administration controllers are small chips which are soldered onto the motherboard of servers inside information facilities. Administrators depend on these highly effective controllers for varied distant administration capabilities, together with putting in updates, monitoring temperatures and setting fan speeds accordingly, and reflashing the UEFI system firmware that enables servers to load their working methods throughout reboots. BMCs present these capabilities and extra, even when the servers they’re related to are turned off.
Code execution contained in the BMC? Yup
The potential for vulnerabilities in BMCs to be exploited and used to take management of servers hasn’t been misplaced on hackers. In 2021, hackers exploited a vulnerability in BMCs from HP Enterprise and put in a customized rootkit, researchers from Amnpardaz, a safety agency in Iran, reported that 12 months. ILObleed, because the researchers named the rootkit, hid contained in the iLO, a module in HPE BMCs that’s quick for Integrated Lights-Out.
ILObleed was programmed to destroy information saved on disk. If admins reinstalled the working system, iLObleed would stay intact and reactivate the disk-wiping assault repeatedly. The unknown attackers accountable took management of the BMCs by exploiting a vulnerability HPE had fastened 4 years earlier. In June, the National Security Agency urged admins to comply with steerage to stop such incidents.
Researchers from safety agency Binarly on Tuesday disclosed seven high-severity vulnerabilities in the IPMI (Intelligent Platform Management Interface) BMC firmware. Supermicro has acknowledged the vulnerabilities, thanked Binarly, and offered patching data right here. There’s no automated approach to set up the updates. Supermicro stated it’s unaware of any malicious exploitation of the vulnerabilities in the wild.
One of the seven vulnerabilities, tracked as CVE-2023-40289, permits for the execution of malicious code contained in the BMC, however there’s a catch: Exploiting the flaw requires already obtained administrative privileges in the net interface used to configure and management the BMCs. That’s the place the remaining six vulnerabilities come in. All six of them allow cross-site scripting, or XSS, assaults on machines utilized by admins. The exploit state of affairs is to make use of a number of of them in mixture with CVE-2023-40289.
In an e mail, Binarly founder and CEO Alex Matrosov wrote:
Exploiting this vulnerability requires already obtained administrative privileges in the BMC Web Interface. To obtain it, a possible attacker can make the most of any of the XSS vulnerabilities we discovered. In such a case, the exploitation path will appear like this potential state of affairs:
1. an attacker prepares a malicious hyperlink with the malicious payload
2. contains it in phishing emails (for instance)
3. when this click on is opened, the malicious payload shall be executed inside BMC OS.
Admins can remotely talk with Supermicro BMCs via varied protocols, together with SSH, IPMI, SNMP, WSMAN, and HTTP/HTTPS. The vulnerabilities Binarly found might be exploited utilizing HTTP. While the NSA and plenty of different safety practitioners strongly urge that BMC interfaces be remoted from the Internet, there’s proof that this recommendation is routinely ignored. A latest question to the Shodan search engine revealed greater than 70,000 situations of Supermicro BMC which have their IPMI net interface publicly obtainable.
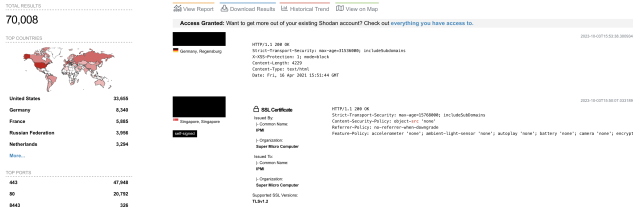
The street map for exploiting the vulnerabilities in opposition to servers with Supermicro interfaces uncovered this manner is illustrated beneath:
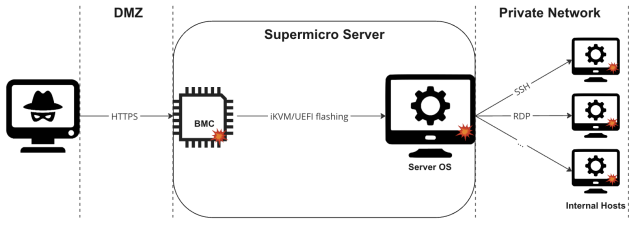
In Tuesday’s put up, Binarly researchers wrote:
First, it’s doable to remotely compromise the BMC system by exploiting vulnerabilities in the Web Server element uncovered to the Internet. An attacker can then achieve entry to the Server’s working system through authentic iKVM distant management BMC performance or by flashing the UEFI of the goal system with malicious firmware that enables persistent management of the host OS. From there, nothing prevents an attacker from lateral motion inside the inside community, compromising different inside hosts.
All the vulnerabilities Binarly found originate in IPMI firmware third-party developer ATEN developed for Supermicro. While ATEN patched CVE-2023-40289 six months in the past, the repair by no means made its means into the firmware.
“This is a supply chain problem because it can be other BMC vendors that can be potentially impacted by these vulnerabilities,” Matrosov wrote.