It isn’t straightforward to think about working with out expertise. Whether it’s throughout work hours or in free time, expertise has been rooted in our each day actions which we carry out.
The identical goes for the HR sector. It isn’t any extra simply administrative work; it has positioned itself in a strategic place to drive the expansion of organizations. HR Software Development has revolutionized how the enterprise manages the HR duties earlier evaluate to now.
Technology is the important thing factor that has modified how the HR sector works. Advancements in HR Software Development have enabled automation in work processes that had been earlier accomplished manually.
Recent Trends in HR Software Development
- However, improvements in expertise additionally carry challenges with them. Data safety and privateness have been sizzling matters these days. Governments worldwide implement strict guidelines and laws to make sure folks’s knowledge are protected and not misused.
- Technology is not only restricted to engineers and programmers. Every worker in all departments relies on expertise to do their job. Everyone must have a fundamental understanding of privateness and safety
- According to a report revealed on Financial Express, small companies are the first targets for cybercrime gangs. Small firms prioritize the best way to make earnings and broaden their enterprise, leaving cybersecurity in a susceptible spot.
Identifying Key Data Security and Privacy Challenges in HR Software Development
-
Remote Working Conditions
Employees working remotely want to make sure they don’t hook up with unsecured web. During COVID-19 as Work from dwelling changed places of work, such incidents occurred extra steadily.
Connecting to public Wi-Fi may very well be dangerous, resulting in the leak of delicate data like private cellular numbers, worker knowledge, and many others. HR professionals ought to be sure that workers take precautions whereas understanding of the workplace.
-
Third-Party Integration Services
Businesses combine HR software program with different programs for numerous necessities. It is helpful for companies in day-to-day operations. However, it additionally will increase knowledge publicity. While choosing third-party integrations, organizations ought to guarantee they’re choosing trusted distributors and following knowledge switch protocols.
Holding pointless knowledge will not be sensible and will increase the probabilities of unauthorized entry. Organizations ought to implement knowledge deletion insurance policies to safeguard worker data.
As extra and extra workers want to make use of their very own gadgets, firms implementing Bring Your Own Device options are on elevated safety dangers. There is all the time a worry that others may leak delicate details about payroll and advantages, exposing workers’ knowledge to different organizations.
Even if the corporate’s system is safe, hijackers can entry delicate data in real-time by way of the Internet of Things (IoT). In these instances, The hacker needn’t even acquire entry to the cloud.
Major Repercussions Related to Data Breach
The very first thing that involves thoughts when such an incident happens is lack of belief. The breach impact not solely impacts the group but in addition extends outward. Clients may terminate or withhold the tasks if the state of affairs turns into uncontrolled.
Skilled workers may resign from the group leaving a scarcity of expertise. Thereafter, even new workers wouldn’t wish to be part of the corporate as a result of lack of belief.
-
Penalty Imposed by Regulatory Bodies
Organizations failing to fulfill safety norms not solely tarnish belief but in addition face the wrath of regulatory our bodies. In Western international locations just like the US and European Union, the place knowledge safety norms are strict, firms need to pay a lump sum quantity as a penalty.
-
Legal Cost Related to Lawsuits
Companies need to incur bills associated to lawsuits filed by authorities officers and even workers affected by knowledge breaches. These outcome in further burdens for the corporate.
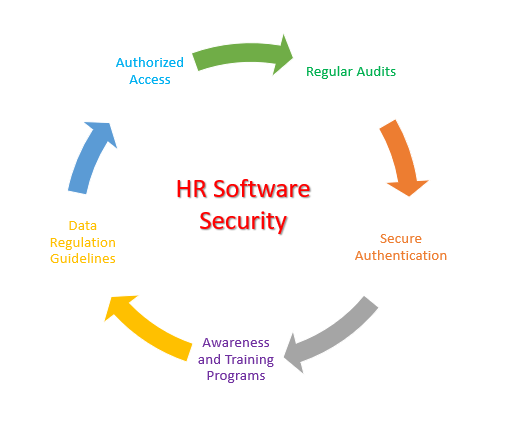
Strategies that may Ensure Data Security and Privacy
-
Conducting Awareness and Training Programs
HR ought to maintain consciousness packages to coach workers about numerous safety dangers that they need to take care in thoughts whereas they don’t seem to be in places of work. Employees who don’t have a lot technical data ought to be explicitly addressed.
This is likely one of the primary duties to be carried out, as in line with a research performed by the World Economic Forum, round 95% of cybersecurity incidents happen attributable to human error.
-
Comprehensive Secure Authentication Process
The knowledge ought to be encrypted with correct authentication strategies and a multi-factor verification course of. Companies ought to go for ISO certification, an inside normal for International Security Management Systems. A framework is created for organizations on how they need to handle their data threat and defend necessary property.
-
Doing Regular Security Audits
Companies should conduct common safety audits to establish vulnerabilities and ache factors in the system. This can assist the safety crew preserve up to date on any malware or leaks that may be solved.
Updating software program can also be essential to make sure bugs are mounted. Hackers attempt to infiltrate the weak areas in previous software program codes. Leaving it open is a dangerous course of and is usually a pricey affair.
-
Being Compliant with Data Protection Regulations
Software Developers ought to be sure that HR Software ought to adjust to related regulatory our bodies like European Union’s General Data Protection Region and the US Act like California Consumer Privacy Act (CCPA).
Being on the brilliant facet would safeguard firms from being in authorized bother and create a tradition of belief.
-
Providing Access Based on Roles
Organizations ought to grant workers entry to delicate knowledge primarily based on their roles and obligations. It ensures that the information is with the licensed particular person. Maintaining common opinions and permissions requires us to keep up knowledge integrity.
Final Thoughts
As time passes, extra challenges will proceed to happen in HR Software Development. Software Developers must always put together themselves for brand new safety threats by figuring out potential challenges and implementing extra strong methods.
With extra folks understanding the significance of information privateness, builders ought to construct software program holding in thoughts the rising significance of information privateness worldwide and the strict laws imposed by governments.
To develop, organizations ought to make selections on revenue maximization and the privateness of workers and shoppers to create long-lasting relationships. Ultimately it’ll result in a safer and safer digital ecosystem for workers, shoppers, and companies.
Featured Image Credit: Provided by the Author; Thank you!

