Apps mimicked by the FluHorse malware. Image credit score Check Point Research
To hijack any 2FA codes despatched, the three apps request SMS entry. With 2FA, a consumer can open an app or web site by typing in a password and a particular code that’s despatched to the consumer’s cellphone by textual content. The faux apps copy the UIs of the true apps however do not do a lot outdoors of accumulating the consumer’s data including bank card data. Then, to make it seem as if some actual processing is happening, the display says “system is busy” for 10 minutes. What’s actually taking place is that 2FA codes are being stolen together with personal data.
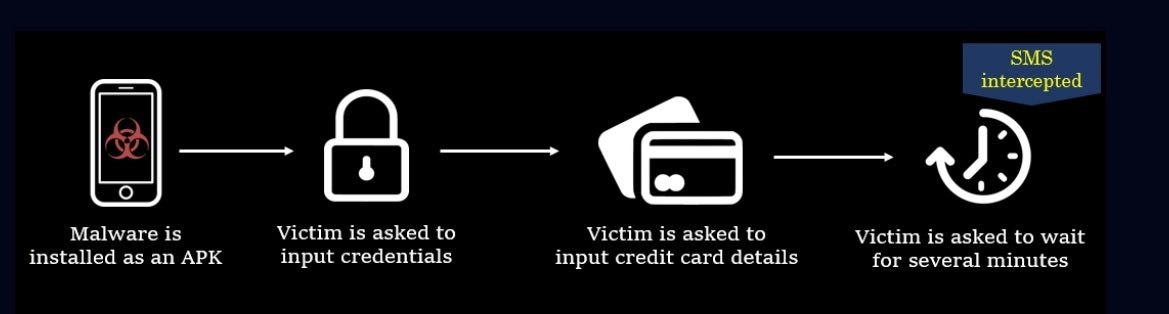
How FluHorse works
According to Check Point, that is an energetic and ongoing risk to Android customers and it’s at all times finest to not give away personal data like bank card numbers and social safety numbers on-line. And simply because this organized assault has been noticed in a unique area of the world, it does not imply that try to be lax on the subject of safeguarding your personal data.

