Getty Images
Researchers have unearthed Linux malware that circulated within the wild for no less than two years earlier than being recognized as a credential stealer that’s installed by the exploitation of not too long ago patched vulnerabilities.
The newly recognized malware is a Linux variant of NerbianRAT, a distant entry Trojan first described in 2022 by researchers at safety agency Proofpoint. Last Friday, Checkpoint Research revealed that the Linux model has existed since no less than the identical 12 months, when it was uploaded to the VirusTotal malware identification website. Checkpoint went on to conclude that Magnet Goblin—the title the safety agency makes use of to trace the financially motivated menace actor using the malware—has installed it by exploiting “1-days,” that are not too long ago patched vulnerabilities. Attackers on this situation reverse engineer safety updates, or copy related proof-of-concept exploits, to be used in opposition to gadgets which have but to put in the patches.
Checkpoint additionally recognized MiniNerbian, a smaller model of NerbianRAT for Linux that’s used to backdoor servers working the Magento ecommerce server, primarily to be used as command and management servers that gadgets contaminated by NerbianRAT hook up with. Researchers elsewhere have reported encountering servers that seem to have been compromised with MiniNerbian, however Checkpoint Research seems to have been the primary to determine the underlying binary.
“Magnet Goblin, whose campaigns appear to be financially motivated, has been quick to adopt 1-day vulnerabilities to deliver their custom Linux malware, NerbianRAT and MiniNerbian,” Checkpoint researchers wrote. “Those tools have operated under the radar as they mostly reside on edge-devices. This is part of an ongoing trend for threat actors to target areas which until now have been left unprotected.”
Checkpoint found the Linux malware whereas researching current assaults that exploit important vulnerabilities in Ivanti Secure Connect, which have been underneath mass exploitation since early January. In the previous, Magnet Goblin has installed the malware by exploiting one-day vulnerabilities in Magento, Qlink Sense, and presumably Apache ActiveMQ.
In the course of its investigation into the Ivanti exploitation, Checkpoint discovered the Linux model of NerbianRAT on compromised servers that had been underneath the management of Magnet Goblin. URLs included:
http://94.156.71[.]115/lxrt
http://91.92.240[.]113/aparche2
http://45.9.149[.]215/aparche2
The Linux variants join again to the attacker-controlled IP 172.86.66[.]165.
Besides deploying NerbianRAT, Magnet Goblin additionally installed a customized variant of malware tracked as WarpWire, a bit of stealer malware not too long ago reported by safety agency Mandiant. The variant Checkpoint encountered stole VPN credentials and despatched them to a server on the area miltonhouse[.]nl.
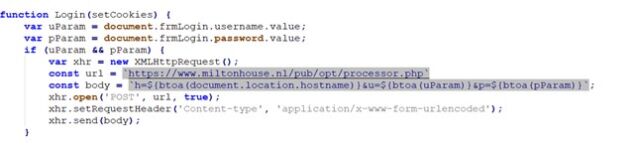
Checkpoint Research
NerbianRAT Windows featured sturdy code that took pains to cover itself and to stop reverse engineering by rivals or researchers.
“Unlike its Windows equivalent, the Linux version barely has any protective measures,” Checkpoint stated. “It is sloppily compiled with DWARF debugging information, which allows researchers to view, among other things, function names and global variable names.”

