A computer system is an integral a part of each workspace. Employees normally carry out most of their job duties immediately on their computer system or via a distant computer.
But there’s numerous delicate and confidential data saved and shared over these interconnected computer systems. So it’s no shock that computer monitoring is important for many companies.
But what is computer monitoring precisely, and the way does it assist your online business?
In this text, we’ll discover computer monitoring, its advantages, the 5 finest software program tools, and a few associated finest practices.
Table of contents
Let’s dive in.
What is computer monitoring?
Computer monitoring, a type of digital monitoring, refers to the processes and techniques used to monitor and report consumer exercise on a PC or computer community.
Employers use computer monitoring to monitor workers’ productiveness, adherence, and conduct on the office. It’s appropriate for each in-office and distant work groups.
Some of the frequent issues employers observe on their workers’ computer systems embrace:
- The consumer title an worker makes use of to log in to their laptops or desktop computer systems.
- User exercise akin to keystrokes, visited web sites, file switch, and so forth.
- Time spent on varied duties throughout work hours.
- Internet and software utilization throughout work hours.
- All inside and exterior communications (immediate messages, emails, and so forth.) by way of the corporate community.
- Location and IP tackle (for a distant worker).
- Storage and different peripheral units like laborious drives, flash drives, printers, and so forth., linked to the computer.
Companies normally retailer worker exercise logs and time information on safe servers as a part of their compliance packages. They might run analytics on this information to determine patterns in worker habits and use the insights to enhance their productiveness.
But how do companies monitor all computer systems within the workspace?
How does computer monitoring work?
Most corporations use worker computer monitoring software program to observe all workstations (on-premise and distant) linked to the corporate community.
Computer monitoring or surveillance software program is any instrument that helps companies preserve tabs on their workers throughout the workplace premises or via distant entry.
These software program tools can fluctuate from a easy time tracker to a complete workforce administration suite with superior monitoring options like:
- Electronic monitoring like display screen seize to take screenshots of workers’ computer screens at common intervals.
- Multi-layer authentication to forestall information and time theft.
- File switch monitoring.
- Print monitoring to observe what’s printed, customers’ capability to print, and so forth.
- User habits analytics to monitor worker exercise and determine potential danger elements.
- GPS monitoring and geofencing on computer systems and cellular units for distant worker monitoring.
So what computer monitoring software program must you get?
5 finest computer monitoring software program
Let’s try the 5 finest software program to monitor your staff’s computer systems:
1. Time Doctor
Time Doctor is a sturdy worker productiveness administration instrument utilized by giant corporations like Verizon in addition to medium and small companies like Thrive Market to monitor and enhance efficiency throughout the corporate.
Key options
Here are a couple of methods Time Doctor might help enhance your workforce monitoring efforts:
A. Transparent time monitoring
Time Doctor gives two efficient time monitoring modes, guide and automated. Tracking worker work hours helps you analyze workflows and gives necessary enterprise insights.
Besides, realizing their work time is being tracked, your workers will probably be much less possible to slack off and stay centered on their jobs.
For guide monitoring, workers want to comply with these easy steps:
- Open the Time Doctor app and add the duty title they’re engaged on.
- Click ‘Start’ to start monitoring time. Time Doctor will now observe your time as you’re employed.
- Click ‘Stop’ to finish the monitoring when you want to take a break or have accomplished the duty.
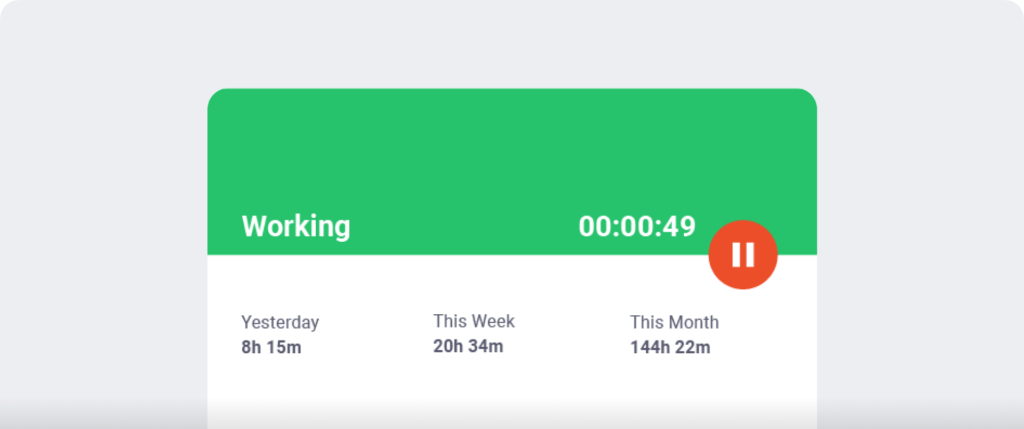
In the automated mode, time monitoring begins as quickly as the worker activates the computer. It permits them to concentrate on the duties with out worrying about beginning the timer. Moreover, it provides the employer invaluable insights into their productiveness and habits.
B. Idle time tracker
Time Doctor additionally helps you observe workers’ idle time.
What’s idle time?
Idle time refers to the interval the place no keystrokes or mouse actions are detected on the worker’s computer.
But why do you want to observe idle time?
Idle time monitoring helps forestall time theft since workers can’t cross off such unproductive minutes as work.
Additionally, it ensures correct funds to your freelance, on-site, and distant work workers for his or her energetic billable hours.
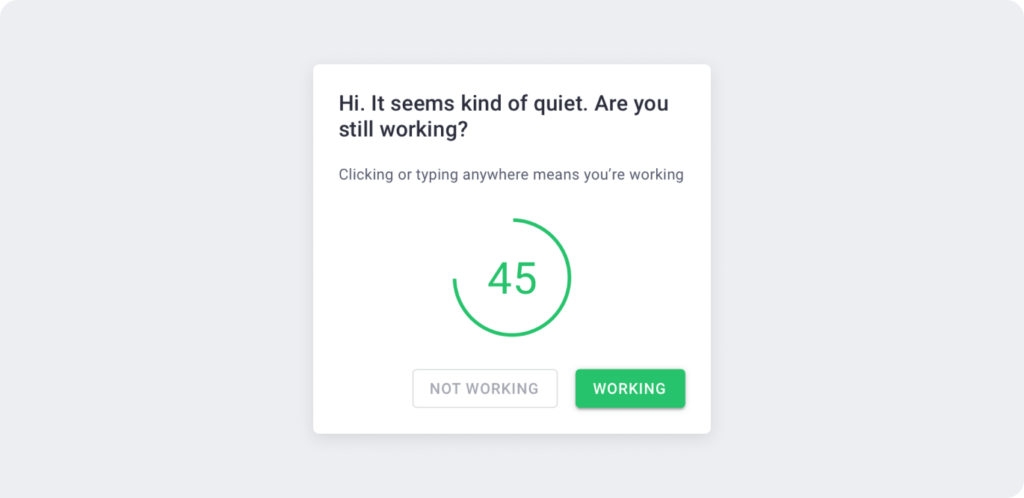
Note: Time Doctor doesn’t report your keystroke or determine which keys you’re urgent to defend consumer privateness.
C. Screencasts (non-obligatory)
With the screencast characteristic, you possibly can take screenshots of an worker’s computer display screen to guarantee they’re working productively on their duties. It’ll additionally provide help to study their keyboard and mouse exercise, giving higher insights into their time and computer utilization.
The keyboard and mouse exercise is the common variety of keystrokes/mouse clicks per minute from the earlier screencast to the present one.
For extra flexibility, customers even have the choice to:
- Download the (chosen) screencasts.
- Change the timezone.
- View solely the screencasts with low or no exercise.
Employees are much less possible to interact in distracting actions akin to social media searching once they know their computer display screen is being monitored throughout working hours.
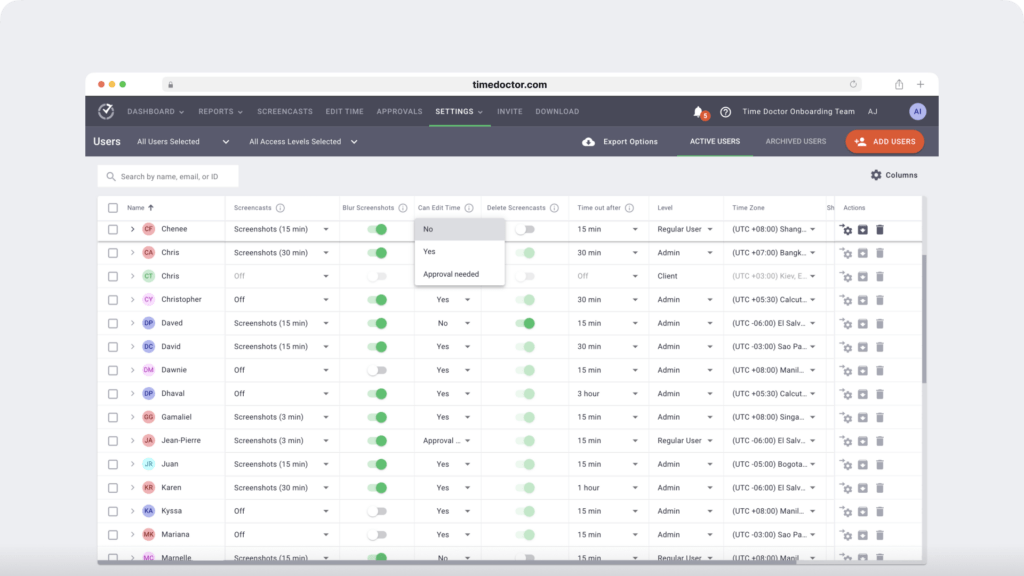
Note: To defend worker privateness, you possibly can blur or delete screenshots with delicate data like passwords.
D. Productivity rankings
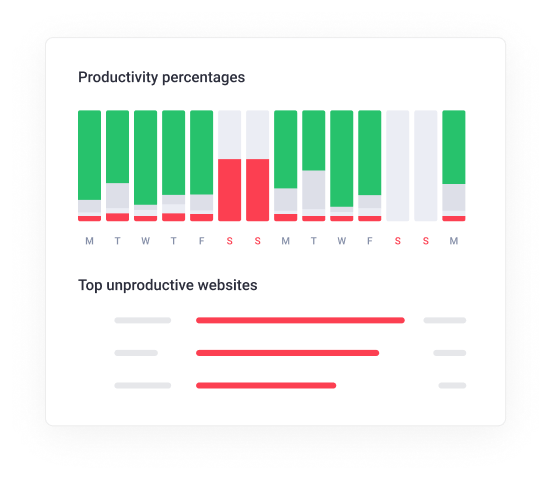
This Time Doctor characteristic permits you to categorize web sites and apps in accordance to their relevance.
You can assign a selected productiveness score to every web site and app, akin to:
- Productive.
- Neutral.
- Unproductive.
- Unrated.
For instance, in case your promoting staff makes use of Facebook to run a selected marketing campaign, you possibly can assign Facebook as a productive app/web site for these workers.
E. Detailed reviews
Comprehensive productiveness reviews might help you observe workers’ computer utilization and different monitoring information and determine potential points. You can then take the required steps to deal with them.
With Time Doctor, you possibly can see detailed and real-time reviews to consider worker efficiency.
For instance, the Web and Application Usage report exhibits workers’ time on completely different apps and web sites throughout the workday.
Managers and admins can see:
- The precise URL of visited web sites.
- The software used.
- Duration of use.
Admins may configure the online and app privateness settings and management the extent of particulars seen within the report. These ranges embrace:
- Off: App won’t observe any web sites visited or apps opened.
- Basic: Reports solely present the URL of the web site touchdown web page and the appliance title.
- Extended: Shows full URLs, web page titles, and software window titles.
- Custom: Shows the identical information as in Extended, however with an possibility to specify URLs for which you solely need the foundation area to be displayed.
Users can view the online and app utilization reviews for a selected date, week, month, or date vary.
Other helpful Time Doctor reviews embrace:
- Activity abstract: View energetic minutes, energetic seconds, unproductive, guide, and cellular time for every worker over a particular interval.
- Hours tracked: Check what number of hours an worker has tracked in a day, week, or throughout a particular interval.
- Timeline report: Shows the time an worker spent working (each day and weekly reviews).
- Projects & duties report: View workers’ time on every particular mission and process.
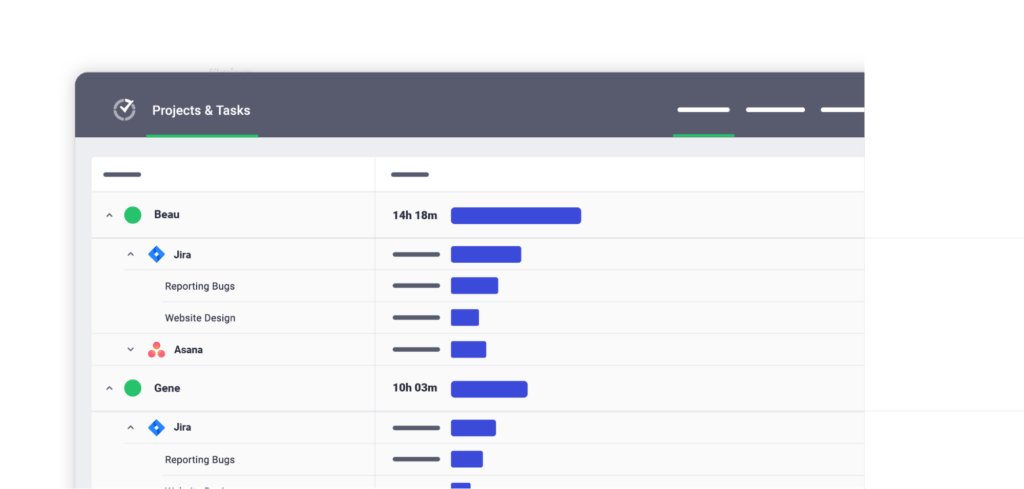
Pricing
Time Doctor gives a free 14-day trial (no bank card required). Paid plans begin at $6.70/consumer per 30 days.
Customer rankings
- G2: 4.4/5 (400+ critiques)
- Capterra: 4.5/5 (530+ critiques)
2. WorkTime
WorkTime is an worker monitoring software program resolution appropriate for all companies and might deal with heavy workloads starting from 1-15000+ computer systems.
Key options
- Monitor worker computer exercise and web utilization for distant and in-office workers.
- Tracks energetic and idle occasions, in addition to login and logouts.
- Gives the choice to retailer monitoring information on the cloud or regionally on firm servers.
- Secures delicate information utilizing encryption and password safety.
- Is compliant with HIPAA requirements.
Pricing
WorkTime gives a free 14-day trial (no bank card required). Paid plans begin at $6.99/worker per 30 days.
Customer rankings
- G2: 4.6/5 (30+ critiques)
- Capterra: 4.4/5 (110+ critiques)
3. ActivTrak
ActivTrak is worker computer monitoring software program that helps groups carry out at optimum ranges. With its computer monitoring options, you possibly can observe worker hours and domesticate wholesome work habits.
Key options
- Managers can view complete and productive work time individually or for groups.
- Shows historic information to set worker productiveness objectives and benchmarks.
- Automated emails to share productiveness insights and different data with the workers.
- Daily, weekly, and month-to-month reviews present worker workload and work patterns.
- Multi-layered safety to preserve delicate data safe and protected.
Pricing
ActivTrak has a 14-day free trial (no bank card is required). Paid plans begin at $10/consumer per 30 days.
Customer rankings
- G2: 4.4/5 (200+ critiques)
- Capterra: 4.6/5 (500+ critiques)
4. Teramind
Teramind is an worker monitoring instrument with options to analyze worker habits and stop information loss.
Key options
- Real time consumer exercise monitoring to detect and block violation incidents.
- Powerful IT (Information Technology) options for information loss prevention.
- Endpoint safety software program screens consumer exercise and sends alerts once they entry or switch delicate data.
- Admins can outline productive and non-productive apps and web sites.
- Business Intelligence (BI) dashboard to observe worker productiveness metrics.
- Built-in help for compliance with legal guidelines like GDPR and PCI DSS.
Pricing
Teramind gives free trials for 7 days (Cloud-Based) or 14 days (On-Premise). Paid plans begin at $15/consumer per 30 days.
Customer rankings
- G2: 4.6/5 (130+ critiques)
- Capterra: 4.6/5 (80+ critiques)
5. InterGuard
InterGuard is an worker monitoring resolution with productiveness monitoring options for on-premise and distant groups.
Key options
- Sends alerts for key phrase triggers and suspicious computer exercise.
- Allows admins to create role-based net entry and see detailed on-line exercise reviews.
- Helps retrieve delicate recordsdata, delete stolen information and lock a tool in case of insider menace incidents.
- Lets customers monitor Android, iOS, Mac, Windows, and Citrix units utilizing a single interface.
- Offers program, e mail, and file exercise monitoring.
Pricing
Contact InterGuard Employee Monitoring Software to get hold of present pricing.
Customer rankings
- G2: 3.3/5 (7+ critiques)
- Capterra: 3.9/5 (30+ critiques)
Comparison desk: Best computer monitoring software program
| Software | Key options | Best for | Pricing (Per consumer) | Free trial | G2 score |
| Time Doctor | Time & exercise monitoringIdle time detectionWebweb site & app utilization monitoringScreenphotographs (non-obligatory)Productivity reportsPayroll integration | Small to giant companies | $6.70/month | 14 days | 4.4/5 (4300+ critiques) |
| ActivTrak | AI-powered productiveness monitoringAutomated alertsHistorical productiveness developmentsWebweb site & app monitoringEmployee workload stability insights | Mid to giant groups | $10/month | 14 days | 4.4/5 (200+ critiques) |
| WorkTime | Employee exercise & web utilization monitoringIdle & energetic time trackingHIPAA-compliant information securityLocal & cloud information storageAutomated time reviews | Healthcare & compliance-focused groups | $6.99/month | 14 days | 4.6/5 (3010+ critiques) |
| Teramind | Insider menace detectionAdvanced safety compliance (GDPR, PCI DSS)Screen recordingKeystroke & file switch monitoringBusiness intelligence (BI) dashboard | Enterprises & security-sensitive industries | $10/month | 7-14 days | 4.6/5 (13050+ critiques) |
| InterGuard | Keyword alerts for suspicious activityRole-based net accessDevice lock & distant file deletionMulti-device help (Windows, Mac, iOS, Android)Email, file, and app monitoring | Remote & hybrid workforce | $25/month | No free trial | 3.3/5 (75+ critiques) |
Check out this informative article to be taught extra about worker monitoring.
Now, let’s discover a couple of methods worker computer monitoring might help your online business.
Why must you monitor computer systems on the office?
Monitoring the computer exercise of your workers will provide help to:
1. Improve worker productiveness
Employees could get distracted and have interaction in unproductive actions throughout their working hours. This impacts their productiveness and the corporate’s total effectivity.
But once they know their computer exercise is being monitored, they might chorus from accessing non-work-related web sites and purposes. This will ultimately lead to maximizing their productive time throughout the workday.
Besides, supervisors can spot work errors in actual time with exercise monitoring and information the workers accordingly.
Additionally, managers can use time utilization reviews to determine poor work patterns and the largest time-wasters throughout work hours. They can then assist underperforming workers right such points and enhance effectivity.
And since these tools normally have distant monitoring capabilities, you possibly can simply observe the actions of your distant employees and workers.
2. Prevent unethical practices
While corporations normally take steps to defend themselves from exterior threats and safety breaches, they typically fail to acknowledge the potential danger elements inside.
It’s not unusual for workers to interact in practices that may put firm information in danger and negatively impression its operations. A safety challenge like this is normally often called an insider menace.
These safety dangers can happen both deliberately or unintentionally when workers:
- Share enterprise secrets and techniques, purchasers’ or workers’ private information, and so forth., with exterior sources.
- Access purposes and web sites that compromise information and computer community safety.
- Perform or facilitate information or safety breaches and time thefts.
Effective worker monitoring can reduce such coverage violation incidents by continually screening computer systems for suspicious habits.
Advanced PC monitoring software program makes use of AI and machine studying to analyze worker habits. With these insights, corporations can anticipate potential danger elements and take proactive measures to forestall them.
3. Ensure compliance with legal guidelines
Depending on the character of labor, companies might have to adhere to federal legal guidelines and safety requirements akin to:
But as a supervisor, you might discover it difficult to make sure that your workers adhere to these tips.
Thankfully, most computer monitoring software program permits corporations to customise the instrument to implement compliance with such legal guidelines and requirements.
For instance, healthcare organizations can use an worker monitoring instrument that stops the misuse of non-public well being data (PHI) in accordance with HIPAA.
However, to totally reap the advantages of computer monitoring tools, you could deploy the expertise options rigorously.
Let’s check out a number of the handiest methods to introduce and make use of a computer monitoring system.
Computer monitoring finest practices
Here are some methods to monitor your groups safely and successfully:
- Identify your online business and compliance necessities to choose the suitable computer monitoring software program on your wants whereas making certain worker privateness.
- Be clear about your computer monitoring coverage and search workers’ consent.
- Choose a non-invasive PC monitoring software program that protects the workers’ privateness and ensures endpoint safety.
- Do not observe or report an worker’s delicate information, akin to private data and passwords.
- Follow community monitoring and different safety tips prescribed by PCI DSS to complement your computer monitoring software program.
- Regularly test for analytics-based insights to make significant modifications to worker workflow and safety coverage.
- If you’ve got a staff of completely distant employees, search for a software program resolution that helps you interact your workers higher.
Key takeaways
Monitoring worker computer exercise utilizing computer surveillance software program might help you enhance productiveness, compliance, and information safety.
You can use the very best practices shared above to construct a stable but pleasant worker monitoring program and obtain your online business objectives.
While all of the office surveillance tools talked about above can work, Time Doctor stands out with highly effective options like computer exercise monitoring, time monitoring, mission administration, and extra.
So why not get a demo of Time Doctor to get began at the moment?
Frequently requested questions (FAQs)
1. Is computer monitoring authorized?
Yes, computer monitoring is authorized in most international locations, however companies should adjust to privateness legal guidelines like:
- U.S. – Employers can legally monitor company-owned computer systems however should notify workers in states like California and Delaware.
- EU (GDPR) – Employers should get hold of specific consent earlier than monitoring workers.
- Canada (PIPEDA) – Employers should show that monitoring is essential and cheap for enterprise operations.
- Australia (Workplace Surveillance Act) – Employers should give at the very least 14 days’ discover earlier than monitoring.
Best Practice: Always inform workers about monitoring insurance policies to keep away from authorized dangers.
2. Can employers monitor private units (BYOD coverage)?
If workers use private units (e.g., laptops, telephones) for work, employers can monitor solely work-related actions, however they can not observe private apps, messages, or non-public searching historical past.
Best practices for monitoring BYOD:
- Use cellular gadget administration (MDM) software program to monitor work apps solely.
- Ensure information safety compliance (e.g., GDPR, HIPAA).
- Separate work and private information on units.
What’s unlawful? Tracking non-public messages, GPS location, or private social media accounts with out consent.
3. Can workers see if they’re being monitored?
This relies on the kind of monitoring software program:
- Transparent monitoring (e.g., Time Doctor) permits workers to see when they’re being tracked.
- Stealth mode monitoring runs silently with out workers realizing, however it might violate privateness legal guidelines in some areas.
Tip: Employers ought to at all times talk their monitoring coverage to preserve belief
4. How do corporations monitor worker emails?
Companies can observe work e mail exercise utilizing:
- Email filtering software program to flag delicate key phrases.
- Data Loss Prevention (DLP) tools to forestall sharing of confidential information.
- Email archiving to preserve a report of despatched and acquired emails for compliance.
Legal issues: Employers can monitor work emails, however monitoring private e mail accounts (e.g., Gmail, Yahoo) on firm units could also be unlawful.
5. Can workers bypass monitoring software program?
Yes, some workers try to bypass monitoring, together with:
- Using VPNs to masks their location and searching exercise.
- Using auto-clickers to faux mouse motion.
- Running digital machines (VMs) to create a separate setting.
- Using second screens to do private duties whereas monitoring software program tracks a work-related app.
Prevention suggestions for employers:
- Use AI-based monitoring (e.g., Time Doctor’s Unusual Activity Report) to flag suspicious exercise.
- Implement habits analytics to detect uncommon patterns.
- Restrict unauthorized software program installations on firm units.
8. What are the dangers of computer monitoring?
Although computer monitoring has advantages, it additionally carries dangers:
- Legal points – Violating privateness legal guidelines may end up in fines or lawsuits.
- Employee belief considerations – Excessive surveillance can scale back morale and create a poisonous work setting.
- Cybersecurity dangers – Improper information dealing with can expose worker information to cyber threats.
Solution: Implement clear insurance policies, moral monitoring strategies, and safe monitoring tools.
9. Can computer monitoring software program detect incognito searching?
Yes, many monitoring tools can observe searching exercise even in Incognito Mode by:
- Logging visited URLs earlier than encryption.
- Capturing keystrokes (if enabled).
- Taking periodic screenshots.
- Using DNS monitoring to monitor net requests.
Best tools for browser monitoring:
- Teramind – Detects incognito searching and blocks particular web sites.
- Time Doctor – Provides net utilization reviews with privateness settings.
- ActivTrak – Tracks work-related searching exercise.
What it will probably’t observe: Personal VPN–protected searching or encrypted messaging apps.
10. What industries use computer monitoring probably the most?
Certain industries depend on computer monitoring software program for compliance and safety:
- Finance & banking – To forestall fraud and guarantee PCI DSS compliance.
- Healthcare – To defend affected person information (HIPAA compliance).
- Call facilities & BPOs – To observe agent productiveness and shopper information safety.
- Tech & IT companies – To detect insider threats and defend delicate IP (Intellectual Property).
- Government & protection – To forestall information leaks and improve cybersecurity.
Fact: 80% of Fortune 500 corporations use some type of worker monitoring.
11. How can workers defend their privateness whereas being monitored?
Employees can defend their privateness whereas working beneath computer monitoring by:
- Using private units for personal searching and messages.
- Reading firm insurance policies to perceive what information is tracked.
- Using safe passwords and two-factor authentication (2FA) to forestall unauthorized entry.
- Logging out of non-public accounts on work units.
- Asking HR about information retention insurance policies to know the way lengthy their information is saved.
Tip: Companies ought to permit cheap privateness protections to construct belief with workers.

Liam Martin is a serial entrepreneur, co-founder of Time Doctor, Staff.com, and the Running Remote Conference, and writer of the Wall Street Journal bestseller, “Running Remote.” He advocates for distant work and helps companies optimize their distant groups.

